Ivan Marković
Security consultant and researcher
Long experience in designing and implementation of security solutions, mainly oriented on web, mobile and embedded applications. Author of penetration testing tools, recognized by OWASP organization and BackTrack Linux distribution. Researching work includes discovery of vulnerabilities of numeral applications and services, and for these, author received public apreciations by Microsoft Company..
POC script for Malware Hunting over the WWW
04.04.2022
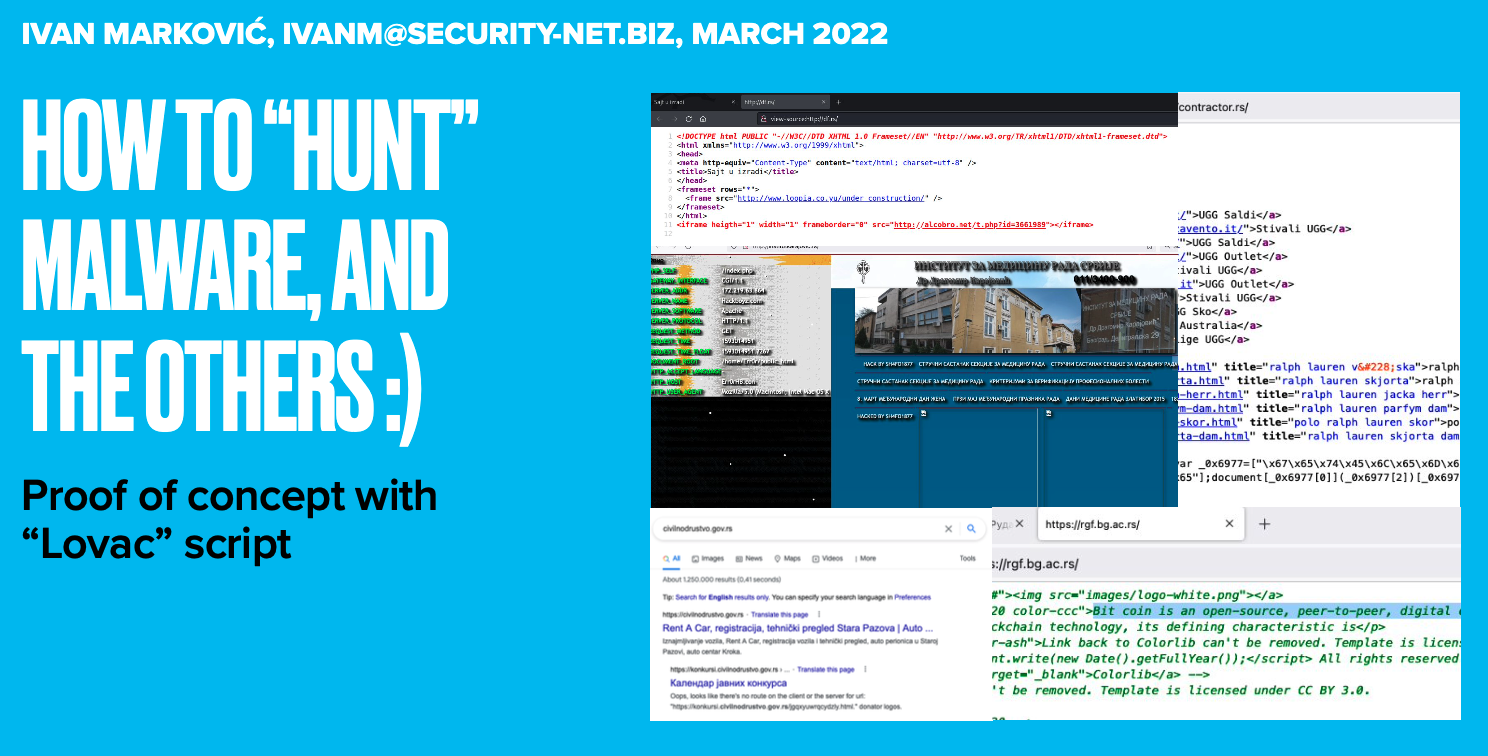
For the purposes of the malware hunting, and threat landscape modeling, over the years I have created several "quick and dirty" scripts to quickly detect the most critical or compromised systems. In the past few weeks I have discovered over 20 compromised locations in less of 24 hours of script work. What is most worrying is that the mean detection time (MTTD) is very high.
This script (with help of ClamAV and little bit of HTML source investigation) already detected more then 20 compromised websites in less than of 24 hours of running. Some examples are:
- IFRAME with malicious link
- Javascript redirection to the Malware
- Javascript hide malicious advertising
- Defaced web site
- Possible Crypto Minner traces
- Private Information Leak
- Misconfigured DNS
Examples:
Discover "co.rs" domains, with minimum length 2 and maximum length 6, try 10k combinations and use only letters "abvgdjezijklm":
# python3 ./lovac.py --tld "co.rs" --min 2 --max 6 --repeat 10000 --chars "abvgdjezijklm"
Discover domains from keyword list and append ".rs":
# python3 ./lovac.py --list LIST_KEYWORDS_OR_DOMAINS.txt --appendtld --tld "rs"
If someone is interested to start with malware hunting, I have published proof of concept script here: https://github.com/Ivan-Markovic/lovac. You can also check the presentation to see what you can discover with a tool.